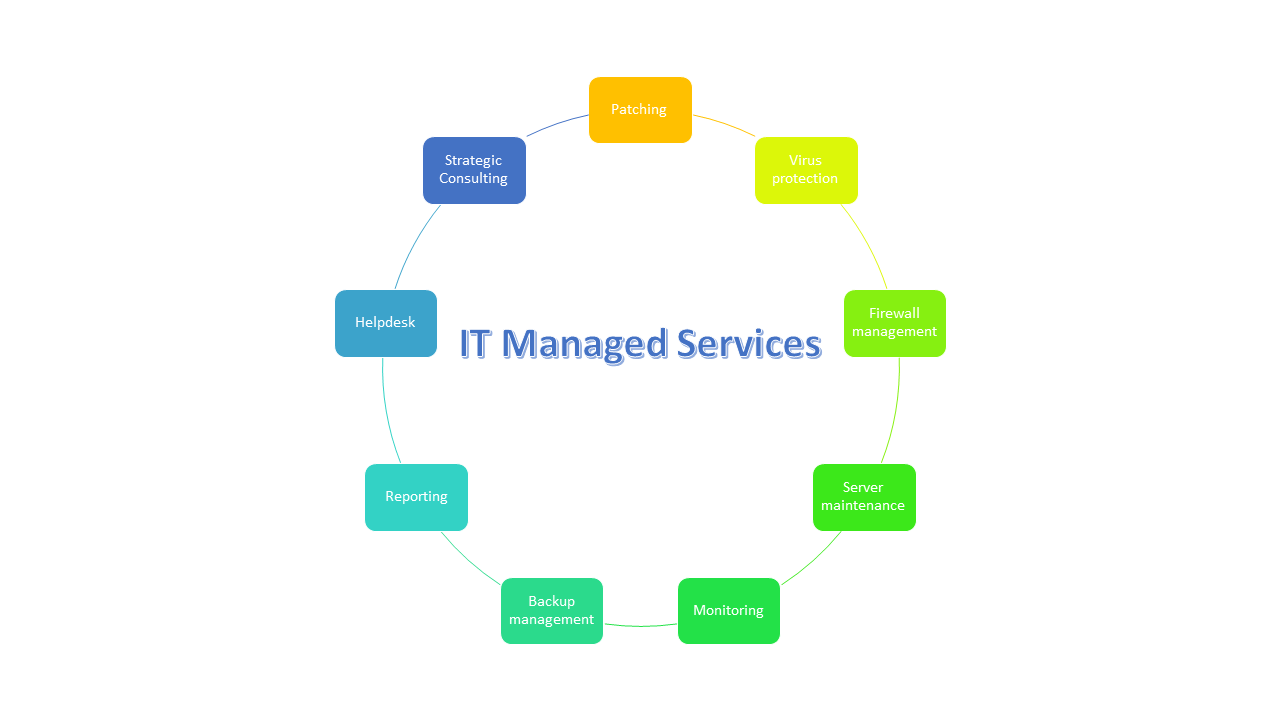
Receptive IT Support Charlotte: Solving Your IT Difficulties
Check Out the Important Function of IT Services in Securing Your Company's Success
In the complex landscape of modern organization procedures, the reliance on Info Innovation (IT) solutions has become vital for making sure the safety and security and success of business. Cybersecurity steps stand as the first line of protection against a selection of electronic risks that can compromise delicate company details and interfere with procedures. Nevertheless, the role of IT solutions goes beyond simple defense; it reaches improving functional effectiveness, safeguarding vital data, and making it possible for the adoption of cutting-edge innovations like cloud options. The tactical assimilation of IT solutions is not just a matter of danger monitoring but a crucial driver of lasting business growth and strength in an ever-evolving electronic age.
Value of Cybersecurity Measures
Guaranteeing durable cybersecurity steps is important for guarding delicate information and keeping the trust of stakeholders in today's interconnected digital landscape. With the increasing regularity and sophistication of cyber threats, companies should prioritize cybersecurity to alleviate dangers efficiently. Executing strong safety and security protocols assists protect against unauthorized gain access to, data breaches, and financial losses.
Cybersecurity procedures encompass an array of practices, including encryption, multi-factor verification, regular safety audits, and employee training. File encryption transforms data right into a protected code, making it unreadable to unapproved users.
Enhancing Functional Efficiency
Given the important value of cybersecurity procedures in securing sensitive information, organizations can better strengthen their functional effectiveness by leveraging innovative IT services. Furthermore, the combination of synthetic knowledge and equipment discovering modern technologies can maximize organization operations through information evaluation, predictive maintenance, and personalized consumer experiences.
In addition, IT services play a critical function in boosting communication channels within a firm. Systems such as VoIP systems and immediate messaging applications enhance real-time interactions, causing quicker decision-making and problem-solving. Furthermore, by making use of project monitoring tools and collaboration software, teams can coordinate successfully, track progression, and fulfill project target dates efficiently. Fundamentally, investing in IT solutions not just enhances operational performance but likewise placements services for continual growth and competition in today's digital landscape.
Securing Delicate Information
Amidst the progressing landscape of cybersecurity hazards, safeguarding sensitive information has become critical for services looking for to keep depend on with their stakeholders. In today's electronic globe, where information violations and cyber-attacks get on the surge, safeguarding delicate details such as consumer information, economic documents, and copyright is vital for keeping an one-upmanship and promoting a favorable online reputation.
To protect sensitive data efficiently, companies should execute durable security measures throughout their IT framework. This consists of file encryption innovations to safeguard information both at remainder and en route, multi-factor authentication to stop unapproved accessibility, regular protection audits and analyses to determine vulnerabilities, and employee training programs to advertise a culture of cybersecurity understanding.
Furthermore, deploying innovative endpoint defense solutions, firewall softwares, and breach discovery systems can assist discover and reduce This Site potential threats before they rise into full-on safety events. By prioritizing the protection of delicate data, businesses can not just abide by governing needs yet likewise construct depend on with customers, companions, and various other stakeholders, eventually adding to long-lasting success and sustainability.
Leveraging Cloud Modern Technology Solutions
The combination of cloud technology services has actually ended up being critical in enhancing the functional efficiency and scalability of modern-day services. By leveraging cloud technology, services can access a wide variety of solutions and resources on a pay-as-you-go basis, eliminating the demand for significant in advance financial investments in hardware and facilities. This scalability allows firms to adjust their IT resources based on transforming demands, making sure optimum performance and cost-efficiency.
Furthermore, cloud modern technology provides improved adaptability, enabling workers to accessibility data and applications from anywhere with an internet connection. This ease of access cultivates collaboration among teams, enhances performance, and sustains remote job setups (IT Support Services Charlotte). Furthermore, cloud remedies give durable data backup and recovery systems, making certain organization continuity in the face of unpredicted events such as natural catastrophes or cyberattacks
In addition, cloud modern technology supplies innovative protection features, including encryption, access controls, and threat discovery devices, securing delicate service data from unauthorized access or breaches. By delegating their IT facilities to credible cloud provider, organizations can concentrate on their core operations while taking advantage of the newest technological advancements and industry ideal methods.
Ensuring Business Continuity
Trick elements of making sure business connection consist of carrying out threat evaluations, establishing extensive connection plans, carrying out backup and healing options, and consistently screening and updating these actions. By proactively dealing with possible threats and vulnerabilities, businesses can minimize the effect of disturbances and swiftly recover from damaging occasions. In enhancement to technical aspects, promoting a culture of preparedness and durability amongst employees is similarly crucial for reliable organization connection monitoring. Ultimately, focusing on service continuity not only safeguards operations however likewise improves general business durability check this and competition in the market.
Conclusion
In conclusion, IT services play a vital function in securing organization success by applying cybersecurity procedures, enhancing operational efficiency, safeguarding delicate data, leveraging cloud technology options, and making sure service continuity. By buying IT solutions, companies can protect themselves from cyber dangers, improve their operations, and maintain the integrity of their data. It is important for companies to prioritize IT solutions to stay competitive and safeguard their lasting success.
Given the essential value of cybersecurity steps in guarding delicate information, companies can better boost their functional effectiveness by leveraging cutting-edge IT services. Additionally, cloud remedies provide durable information backup and healing mechanisms, ensuring business connection in the face of unanticipated events such as natural catastrophes or cyberattacks.